Last updated on 16 june 2022 by CellSpyAustralia
Find My Phone | Find My App: Everything to Know
Have you lost your phone? Fret no more, for the following guide will help track down that missing device. This guide is designed to walk through all of the Find My features on iPhone and iPad, including those introduced with the iOS 15 update.
In this article I’ll show how to use various tools available online in order find my Android Smartphone if I’m ever separated from its enclosure (case). As long as there is mobile internet access available .
Track any phone location by its number:
It’s stressful to lose any kind of device, be it phones or tablets. This is even more true if you’re trying to help someone else find their lost gadget! Having a personal mobile device can make things much easier though as we’ll see in this guide about how best practices should work for helping friends and family members get back on track after losing their own gadgets too quickly without necessarily being able locate them first via GPS tracking apps (though there are some great ones out right now).
How to Find Lost or Stolen Personal Devices
Learn how to find a dead iPhone by enabling the Find My iPhone last known location feature, how to find the last location of an iPhone, even if it’s dead or offline, what to do once you’ve located your lost iPhone, and how to find an iPhone without Find My iPhone.
Does Find My iPhone work when a phone is dead? Yes, if you’ve set up the Find My iPhone last known location feature. If you don’t have this feature turned on, it will be much harder to find an iPhone that is dead. The catch is that you need to have turned this feature on before your iPhone was lost.
Track any phone number with Scannero.io
How Do I Find My iPhone, iPad, or Other Apple Device?
Do you know where your missing phone is? If so, Apple has the perfect solution for finding it, you can use the Find My app through Apple’s iCloud service. The Find My app allows users to locate their lost device through iCloud and plays loud noises or leaves messages if found in order to get back on track with what happened BEFORE-hand! One of its most exciting features is being able turn off privacy settings on all your family members’ devices which means that they won’t be able hide tracks anytime soon because local detectors are used across every single personal computer at once (and this includes Macs!).
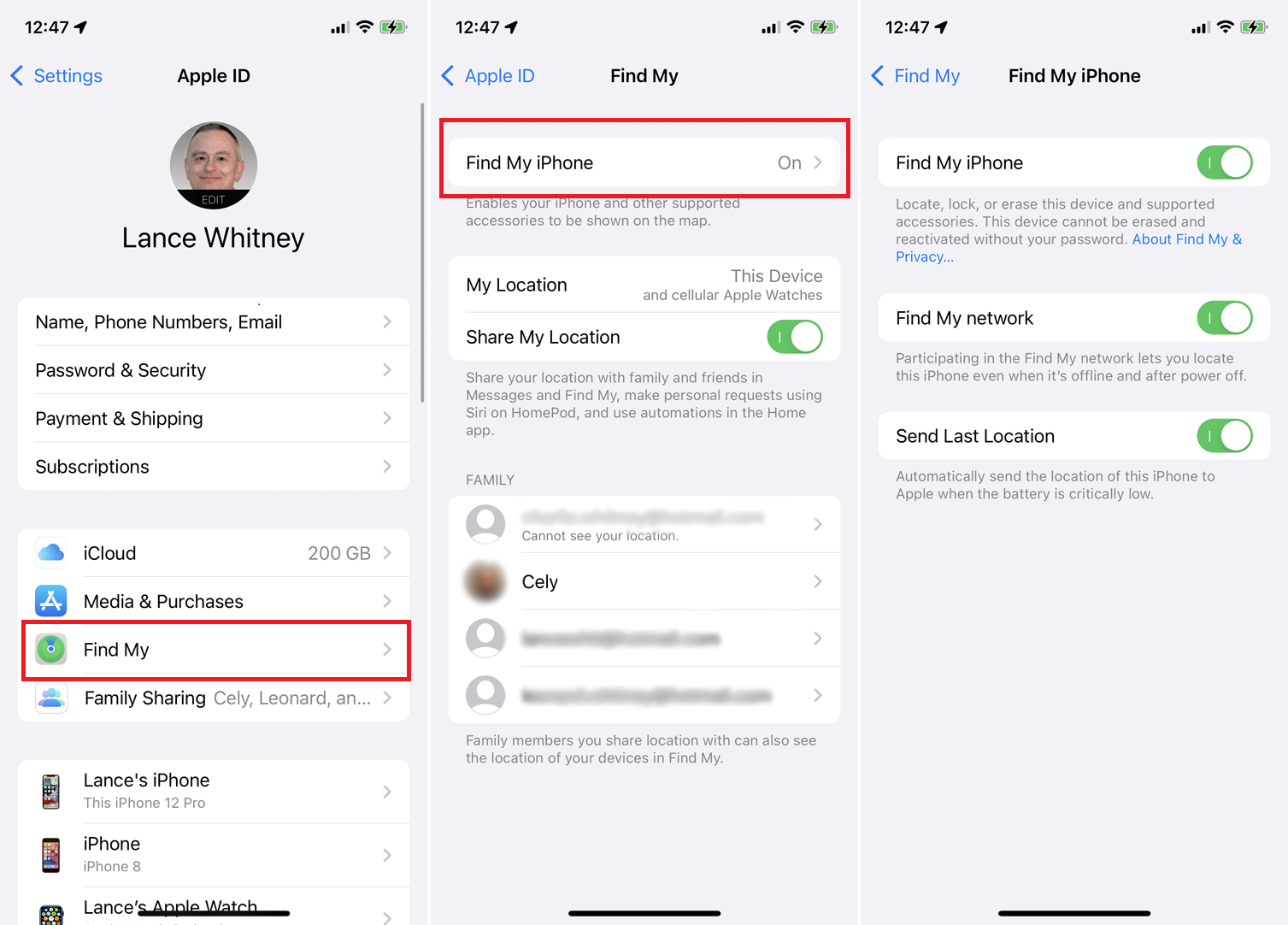
The Find My app is a great way to track your personal devices, but it has one major drawback. The only thing that can be tracked by this service are offline movements–and you need privacy settings on iOS in order for them locate an iPhone or iPad when they’re not connected wires up!
Make sure that your device’s privacy settings allow for Find My functionality or else you won’t be able to locate it using the service.
Enable Family Sharing on iPhone
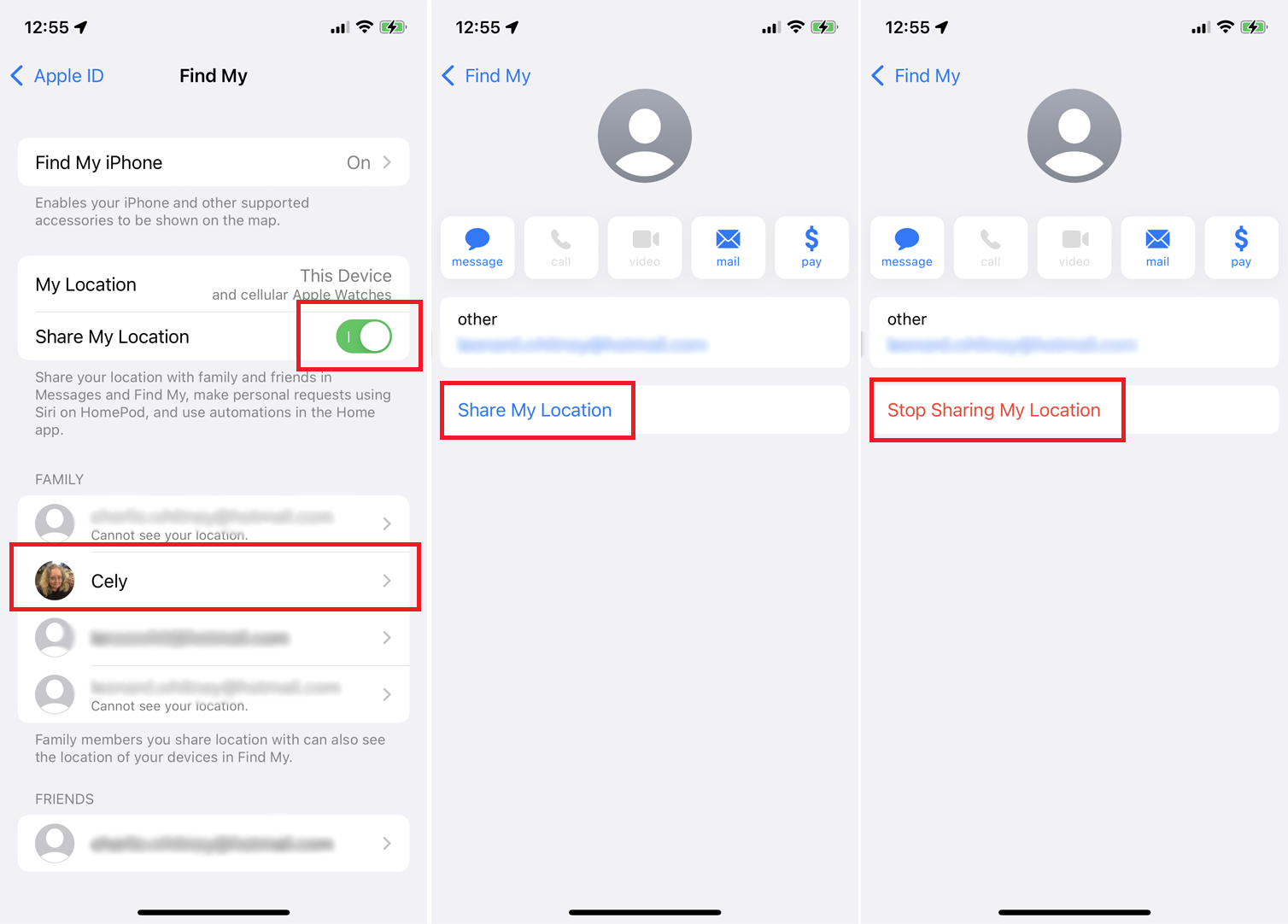
Location sharing is a great way to keep in contact with friends and family. You can use the Find My feature on your phone, as well! Just go Settings > Find My > Share My Location so that they know where you are at all times- no matter what happens (or doesn’t happen).
You may also want to enable Family Sharing, which allows participating family members to use their Apple device to see the location of your devices. To check the sharing status of a family member, tap their name, then tap Share My Location to share it with this person. To stop sharing your location with someone, select them and tap Stop Sharing My Location.
Locate a Lost Device With Family Sharing
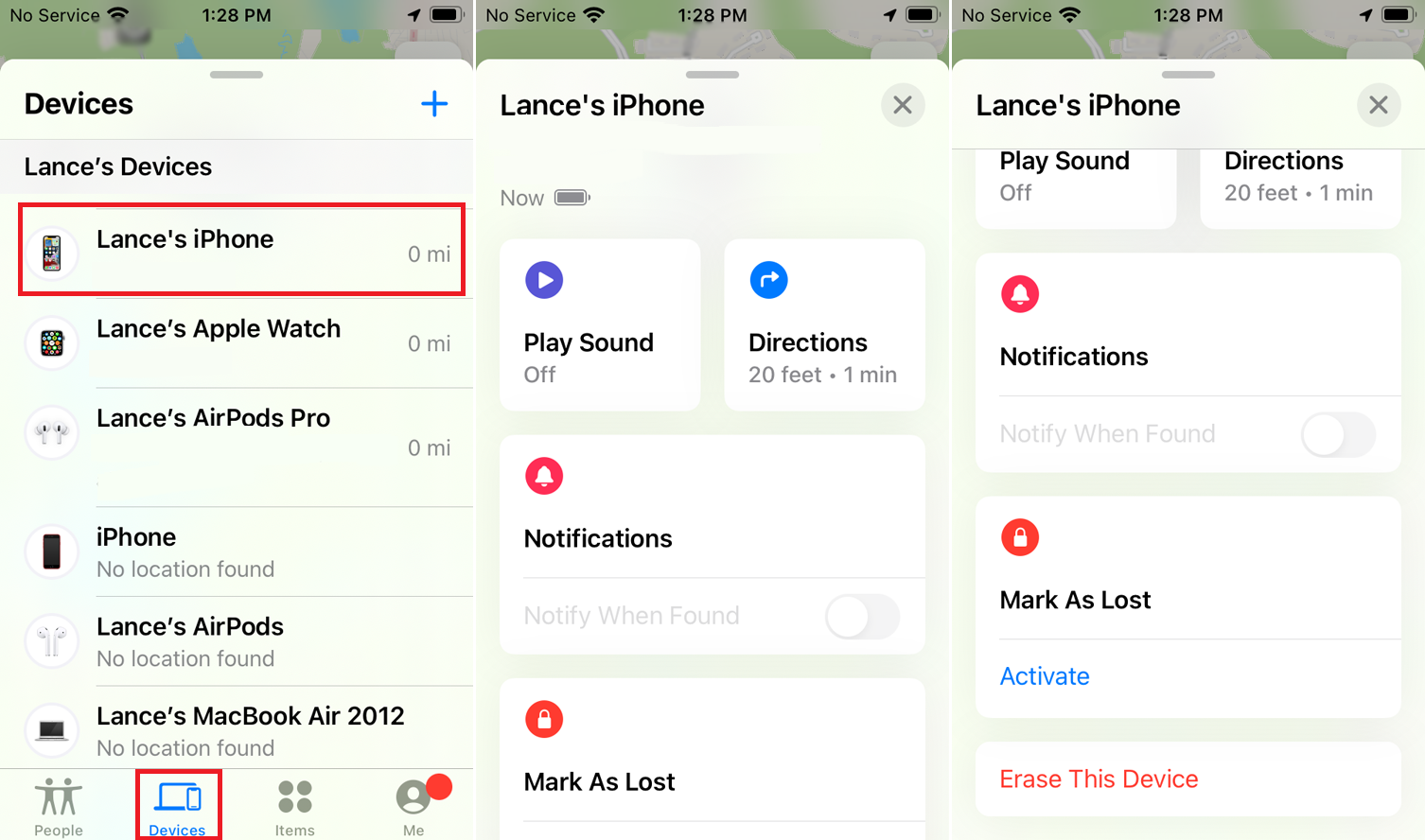
Assuming you have Family Sharing empowered, you can utilize the iPhone or iPad of a relative. Open the Find My application on their gadget and swipe down the sheet of identified gadgets. The application should show every one of the gadgets enrolled under your name; select your missing gadget.
How Do I Find My Android Phone or Tablet?
If you need to find your Android phone or tablet, there are a few tools at your disposal. No matter what type of device it is that holds the title “Google Phone” in its hands (and who could blame anyone?), they can access Google’s Find My Device service for assistance tracking down their lost-in-the Woods gadgets with just some clicks on screen and sound waves sent through headphones! From here all users have different options depending upon how much security versus personal info theft prevention matters most: Play an alerting noise so nearby people know where things may be located; make sure everything remains locked up tight until someone returns them–even completely wipe any saved data if desired
Unfortunately, there are some contexts in which Find My Device will not work. For instance the device must be signed into a Google account and have appropriate permissions selected; that said if it’s offline then your service won’t function either way! However Samsung Android devices come with an exclusive “Find my Mobile” system through their proprietary software platform called Knox – this includes additional options such as ‘offline finding’ mode like Apple’s available on iOS 8 beta releases for example
How Do I Find Feature Phones, Or Any Other Device That Does Not Run iOS or Android?
You will have a much more difficult time recovering from device loss if you lose an iOS or Android-based phone. However, it is not impossible to find your missing smartphone – especially with some preparation beforehand!
If you have recorded the IMEI (International Mobile Equipment Identity), MEID or ESN number from your lost mobile device and submit it to a local police station, this will allow officials there access in finding out what kind of handset was stolen. Additionally if reported correctly with carrier support can block service for that specific country where an initial theft occurred as well! Moreover, you can block mobile service in the country where a device was initially obtained by reporting the IMEI number to your carrier.
How To Find Lost or Stolen Business Devices
If you’ve lost your workplace’s tablet, there are some additional strategies that come into play. For example: did the device ever have a tracking app on it? What about geofencing – can this be used as another form of beacon signal for when we need our phones back most urgently!
Check for Manufacturer-Specific Tools Phone Locator Tools
Heavy-duty device manufacturers are creating their own tools to make locating devices in tough environments easier. For example, Zebra created the Device Tracker as a solution for difficult location problems when working with ruggedized equipment that needs special care and consideration from management due its high usage rates among other things like harsh conditions or large scale use by construction crews who often go beyond what is expected of them every day on jobs around America
The Device Tracker from Zebra is an easy-to use, ruggedized tool that makes locating your lost or stolen device quick and simple. With this powerful little gadget you will never have to worry about losing another important piece of equipment again!
Use The Help of Mobile Device Management
At work, you might not always be able to find your phone. And if it’s lost or stolen in the first place then finding that pesky device can feel impossible- until now! With mobile device management software (MDM) on hand from companies like Apple and Google; employers are provided with tools they need so their employees never again go missing without notice– all thanks to this reliable system which allows workers’ personal devices stay put while still providing them access when needed most through remote wiping capabilities .
With MDM software, you can ensure every device has a complex password and location boundaries. If they go outside of these limits set by administrators then it will send an alert to the user so their missing phone won’t be too hard for them find again!
Admins can also set up protections regarding network connection status. If device tries to connect on a non-secure Wi-Fi, admins will receive a notification and this may deter or stop theft from happening within your company’s walls!
Your company needs to have MDM software in place if you want your employees’ work done efficiently. If not, make sure the admin gets on board with this idea and get started today!